Although today’s cryptographic systems remain robust against classical attacks, the advent of quantum computing threatens to upend the security foundations upon which our digital world rests. Not only are state actors investing billions in quantum R&D, but tech giants and startups alike are racing to develop quantum processors capable of breaking RSA and ECC within hours or even minutes. Therefore, Post-Quantum Cryptography (PQC) has emerged as a critical frontier in cybersecurity, promising encryption algorithms that are resistant to quantum attacks.

check out more like this: techntop
The Quantum Threat to Classical Cryptography
To begin with, quantum computers exploit principles like superposition and entanglement to solve certain problems exponentially faster than classical machines. For example, Shor’s algorithm, developed in 1994, can factor large integers in polynomial time. Consequently, it can break RSA, DSA, and ECC, all of which underpin digital signatures, HTTPS, VPNs, and blockchain protocols.
As a result, even though current quantum systems lack sufficient qubits and error correction to pose an immediate threat, future advances could render today’s encrypted data vulnerable to “harvest now, decrypt later” attacks. Consequently, the need for quantum-safe encryption has never been more urgent.

What is Post-Quantum Cryptography?
Post-Quantum Cryptography refers to cryptographic algorithms that are secure against both classical and quantum attacks. Unlike quantum cryptography, which relies on quantum mechanics, PQC operates on conventional hardware, making it more practical for real-world deployment.
Importantly, PQC algorithms aim to replace public-key cryptosystems while preserving critical properties such as confidentiality, integrity, and authentication. Accordingly, the algorithms must withstand not only quantum-based factorization but also new kinds of cryptanalytic techniques.
Categories of Post-Quantum Algorithms
To understand the landscape better, let us explore the five main categories of PQC:
1. Lattice-Based Cryptography
Lattice problems, such as Learning With Errors (LWE) and Shortest Vector Problem (SVP), are believed to be hard even for quantum computers. Algorithms like CRYSTALS-Kyber and CRYSTALS-Dilithium are finalists in NIST’s PQC competition.
2. Code-Based Cryptography
Rooted in the hardness of decoding linear error-correcting codes, this category includes algorithms like Classic McEliece. While their ciphertext sizes are large, they offer exceptional resilience.
3. Multivariate Polynomial Cryptography
These algorithms involve solving multivariate quadratic equations over finite fields. For instance, Rainbow is a digital signature scheme based on this principle, though it has faced recent cryptanalysis challenges.
4. Hash-Based Cryptography
Using Merkle tree structures and secure hash functions, these schemes (e.g., SPHINCS+) are mainly used for digital signatures. Although relatively slow, they are mathematically simple and extremely secure.
5. Isogeny-Based Cryptography
This newer field relies on the difficulty of finding isogenies between elliptic curves. SIKE was a popular candidate but was recently broken, illustrating that even promising methods require rigorous vetting.
The NIST Standardization Process
The National Institute of Standards and Technology (NIST) began its PQC standardization initiative in 2016. After multiple rounds of evaluation, NIST announced its Round 3 finalists in 2022. These include:
- CRYSTALS-Kyber (Key encapsulation)
- CRYSTALS-Dilithium (Digital signatures)
- FALCON (Digital signatures)
- SPHINCS+ (Stateless hash-based signatures)
As a result, industry leaders are now preparing for integration. Moreover, NIST is expected to publish the final standards by 2024, enabling government agencies and enterprises to begin migration.

Implementation Challenges
Despite their promise, PQC algorithms present practical challenges:
- Performance Overhead: Some algorithms produce large key and ciphertext sizes, impacting bandwidth and storage.
- Compatibility: Integrating PQC into existing protocols like TLS, SSH, and S/MIME requires careful design.
- Hardware Constraints: Resource-constrained devices (e.g., IoT) may struggle with computational demands.
Therefore, hybrid cryptographic schemes, which combine classical and post-quantum algorithms, are gaining traction as an interim solution.
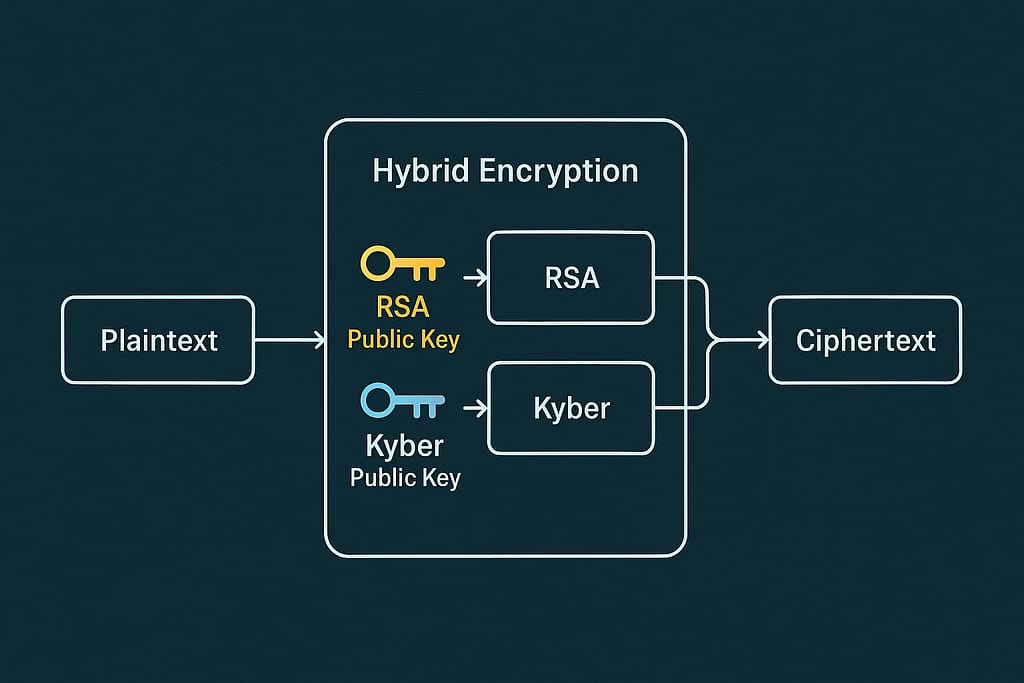
Industry Adoption and Government Initiatives
While academia has led much of the foundational work, the private sector is increasingly involved:
- Google tested Kyber in Chrome to evaluate latency and bandwidth effects.
- Cloudflare has integrated PQC into TLS as part of its research efforts.
- IBM and Microsoft have released developer toolkits for PQC integration.
Simultaneously, governments are taking action. For example, the U.S. Department of Commerce has mandated federal agencies to identify vulnerable systems by 2023. Similarly, the European Union’s ENISA has issued guidelines for quantum-safe migration.
Recent Innovations and Breakthroughs
Several noteworthy developments have advanced the field:
- SIKE broken: A significant 2022 breakthrough demonstrated that isogeny-based cryptography, once a frontrunner, could be vulnerable.
- Efficient implementations: Optimized libraries like liboqs and PQClean make integration easier for developers.
- Hardware acceleration: Efforts are underway to embed PQC in silicon, enabling faster operations in secure elements and TPMs.

Future Outlook and Applications
Given the accelerating pace of quantum advancements, organizations must prepare now. PQC will underpin secure communications, digital identity systems, secure boot in embedded systems, and blockchain.
Furthermore, sectors like finance, defense, healthcare, and telecommunications must plan migration paths to maintain compliance and operational security.
Therefore, forward-looking businesses are not waiting. They are conducting quantum risk assessments, inventorying cryptographic assets, and developing migration plans.

Comparative Analysis: Classical vs. Post-Quantum Cryptography
| Feature | RSA/ECC | Post-Quantum (e.g., Kyber) |
| Security Level | Breakable by quantum | Quantum-resistant |
| Key Size (bits) | 2048 (RSA) / 256 (ECC) | 3840+ |
| Performance (Latency) | High | Moderate |
| Maturity | Decades | Still Emerging |
| Compatibility | Ubiquitous | Requires updates |
While RSA and ECC have served us well, their future is finite. Conversely, PQC represents the next chapter in cryptographic evolution.
Conclusion: Preparing for the Inevitable
In summary, the quantum era is coming, and it will redefine cybersecurity as we know it. Organizations must start now to transition toward PQC. Although the path involves complexity, the cost of inaction could be catastrophic.
Because quantum threats loom large, and since standards are nearly finalized, adopting PQC is no longer optional—it is essential.
Whether you are a CTO, engineer, policy-maker, or cybersecurity enthusiast, your journey toward quantum-resilient security should begin today.


Innovative Approaches to Construction, that shape.
managing construction quality assurance http://www.rapidlybuild.com/the-importance-of-quality-control-in-construction-projects .
for the 2025 Market.
when Finalizing the Deal.
best time to buy a new car https://livelycars.com/ .
A successful business starts with a plan, explore, key points.
how to register a new business http://www.timetobuiseness.com/choosing-the-right-business-structure-llc-corporation-or-sole-proprietorship .
Quality rental without overpaying, for practical travelers.
suzuki swift rental no deposit http://neochorion.com /our-cars/?view=cardetails&carid=15/ .
How to Organize Repair, of technical systems, for better performance.
why electrical equipment fails why electrical equipment fails .
Quality windows and doors from Republic, affordable.
Create the perfect interior, with Republic products.
Classic and modern, by Republic.
by Republic.
Optimal interior solutions, with Republic.
Refresh your interior, with reliable windows and doors.
Energy-efficient windows, from experienced specialists.
Products that impress, from Republic company.
High-quality windows and doors, at reasonable prices.
by Republic company.
Doors and windows for any style, by Republic.
A choice that will make your home better, from professionals.
Buy quality windows and doors with a discount, from experienced specialists.
Doors and windows that will transform your home, with Republic.
New solutions from Republic, for comfortable living.
Choose only the best, by Republic company.
Reduce your energy bills, from Republic.
Your home, your reflection, with Republic.
Experts in windows and doors, with our guarantee.
noise cancelling windows https://wearehoist.com/windows/antinoise-windows/ .
The process of ordering balloons for delivery is now quick and user-friendly. Simply choose your favorite balloon designs online and specify when you want them delivered. This convenience means that anyone can enjoy the beauty of balloons without the hassle.
helium balloons delivered near me https://www.bestwedding-video.com/product-category/helium-balloons .
One significant reason to use a natural terpene blend is its potential to amplify the effects of cannabinoids. The entourage effect describes how terpenes and cannabinoids interact to create a more potent overall effect.
strain specific terpenes http://chinese-shipments.com/ .
https://qrcode-capybara.online/ welcome!
The capybara will be happy if you like the service 🙂
Lovart AI Design Agent seems like a game-changer for streamlining creative workflows. The tri-modal interaction and Figma integration could save designers hours. Worth keeping an eye on! Lovart AI Design Agent